Archive for the ‘hacktivism’ Category
CrisisCamp London, Saturday, 23 Jan. 2010
The London Knowledge Lab is hosting a series of CrisisCamp workshops in January and February. The first of these events will be on this Saturday, 23 Jan. 2010, from 10:00 to 17:00.
A CrisisCamp is an individual event with an overall purpose to create specific tools for a specific problem. Before a CrisisCamp, organizers reach out to responder organizations – governments, non-governmental organizations (NGOs), and others – seeking requests for technological supports. We organize into teams to support those requests. We also develop around things that are just good ideas. What we create is open-source – meaning that it’s free for anyone to use, the labor has been donated, and the user community is encouraged to take it and build on it … to make it work for them. The London Crisis Camp will join the other Crisis Camps in building vital tools for Haiti.
For further details, see the crisiscommons wiki:
http://wiki.crisiscommons.org/wiki/Crisis_Camp_London
The event is organised by Vinay Gupta. If you wish to participate, or have any enquiries, please contact him at: hexayurt+ccl@gmail.com
Hashtag: #crisiscampldn
Short URLs: http://link.lkl.ac.uk/crisiscampldn, http://link.lkl.ac.uk/ccl
Where Does My Money Go? the beauty of open data
The good people of the open knowledge foundation have just released a prototype of their visualisation tool for UK gov spending. This on the same week that the gov announced radical plans for opening their data. Makes the heart soar.
Open data needs to be seen, not just done.
How To Communicate Securely in Repressive Environments
Unlike most of us, it looks like @Patrick Meier knows what he’s talking about. He should, considering he’s doing a Phd at Harvard on “The Impact of the Information Revolution on Authoritarian Rule and Social Resistance: From Information Revolution to iRevolution?”
Patrick has an excelent guide on How To Communicate Securely in Repressive Environments. He keeps it up to date based on his studies and input from readers, and will provide a more detailed guide on request (my guess is that not all requests will be handled equaly).
You should really read it there. If you’re a Farsi speaker, please translate it and email me, I will post it here (or maybe Patrick will want to post it next to the original).
If you’re in a rush, here are a few practical tips. Again, better to refer to the original as it will change over time.
These tactics are listed below along with a number of other important ones. Please keep in mind that tactics are case- and context-specific. They need to be adapted to the local situation.
- Mobile Phones
- Purchase your mobile phone far from where you live. Buy lower-end, simple phones that do not allow third-party applications to be installed. Higher-end ones with more functionalities carry more risk. Use cash to purchase your phone and SIM card. Avoid town centers and find small or second-hand shops as these are unlikely to have security cameras. Do not give your real details if asked; many shops do not ask for proof of ID.
- Use multiple SIM cards and multiple phones and only use pay-as-you go options; they are more expensive but required for anonymity.
- Remove the batteries from your phone if you do not want to be geo-located and keep the SIM card out of the phone when not in use and store in separate places.Use your phone while in a moving vehicle to reduces probability of geo-location.
- Never say anything that may incriminate you in any way.
- Use code.
- Use Beeping instead of SMS whenever possible. Standard text messages are visible to the network operator, including location, phone and SIM card identifiers. According to this recent paper, the Chinese government has established 2,800 SMS surveillance centers around the country to monitor and censor text messages. The Chinese firm Venus Info Tech Ltd sells real-time content monitoring and filtering for SMS.
- Use fake names for your address book and memorize the more important numbers. Frequently delete your text messages and call history and replace them with random text messages and calls. The data on your phone is only deleted if it is written over with new data. This means that deleted SMS and contact numbers can sometimes be retrieved (with a free tool like unDeleteSMS. Check your phone’s settings to see whether it can be set to not store sent texts messages and calls.
- Eavesdropping in mobile phone conversations is technically complicated although entirely possible using commercially available technology. Do not take mobile phones with you to meetings as they can be turned into potential listening/tracking devices. Network operators can remotely activate a phone as a recording device regardless of whether someone is using the phone or whether the phen is even switched on. This functionality is available on US networks.
- Network operators can also access messages or contact information stored on the SIM card. If surveillance takes place with the co-operation of the operator, little can be done to prevent the spying.
- Mobile viruses tend to spread easily via Bluetooth so the latter should be turned off when not in use.
- Using open Bluetooth on phones in group situations, e.g., to share pictures, etc., can be dangerous. At the same time, it is difficult to incriminate any one person and a good way to share information when the cell phone network and Internet are down.
- Discard phones that have been tracked and burn them; it is not sufficient to simply destroy the SIM card and re-use the phone.
- Digital Cameras
- Keep the number of sensitive pictures on your camera to a minimum.
- Add plenty of random non-threatening pictures (not of individuals) and have these safe pictures locked so when you do a “delete all” these pictures stay on the card.
- Keep the battery out of the camera when not in use so it can’t be turned on by others.
- Practice taking pictures without having to look at the view screen.
- Computers/Laptops
- Use passphrases for all your sensitive data.
- Keep your most sensitive files on flash disks and find safe places to hide them.
- Have a contingency plan to physically destroy or get rid of your computer at short notice.
- Flash disks
- Purchase flash disks that don’t look like flash disks.
- Keep flash disks hidden.
- Email communication
- Use code.
- Use passphrases instead of passwords and change them regularly. Use letters, numbers and other characters to make them “c0mpLeX!”. Do not use personal information and changer your passphrases each month. Do not use the same password for multiple sites.
- Never use real names for email addresses and use multiple addresses.
- Discard older email accounts on a regular basis and create new ones.
- Know the security, safety and privacy policies of providers and monitor any chances (see terms of service tracker).
- Browsers and websites
- Turn off java and other potentially malicious add-ons.
- Learn IP addresses of visited websites so that history shows only numbers and not names.
- When browsing on a public computer, delete your private data (search history, passwords, etc.) before you leave.
- When signing up for an account where you will be publishing sensitive media, do not use your personal email address and don’t give personal information.
- Don’t download any software from pop-ups, they may be malicious and attack your computer or record your actions online.
- Do not be logged in to any sensitive site while having another site open.
- VoIP
- Just because your talking online doesn’t mean you are not under surveillance.
- As with a cell or landline, use code do not give salient details about your activities, and do not make incriminating statements.
- Remember that your online activities can be surveilled using offline techniques. It doesn’t matter if you are using encrypted VOIP at a cyber cafe if the person next to you is an under-cover police officer.
- When possible, do not make sensitive VOIP calls in a cyber cafe. It is simply too easy for someone to overhear you. If you must, use code that doesn’t stand out.
- Blogs and social networking sites
- Know the laws in your country pertaining to liability, libel, etc.
- When signing up for a blog account where you will be publishing sensitive content, do not use you personal email address or information.
- In your blog posts and profile page, do not post pictures of yourself or your friends, do not use your real name, and do not give personal details that could help identify you (town, school, employer, etc.).
- Blog platforms like wordpress allow uses to automatically publish a post on a designated date and time. Use this functionality to auto-publish on a different day when you are away from the computer.
- On social networks, create one account for activism under a false but real-sounding name (so your account won’t be deleted) but don’t tell your friends about it. The last thing you want is a friend writing on your wall or tagging you in a photo and giving away your identity.
- Even if you delete your account on a social networking site, your data will remain, so be very careful about taking part in political actions (i.e., joining sensitive groups) online.
- Never join a sensitive group with your real account. Use your fake account to join activism groups. (The fake account should not be linked to your fake email).
- Don’t use paid services. Your credit card can be linked back to you.
- File sharing
- Use a shared Gmail account with a common passphrase and simply save emails instead of sending. Change passphrase monthly.
- For sharing offline, do not label storage devices (CDs, flash drives) with the true content. If you burn a CD with an illegal video or piece of software on it, write an album label on it.
- Don’t leave storage devices in places where they would be easily found if your office or home were searched (i.e., on a table, in a desk drawer).
- Keep copies of your data on two flash drives and keep them hidden in separate locations.
- When thinking of safe locations, consider who else has access. Heavily-traveled locations are less safe.
- Don’t travel with sensitive data on you unless absolutely necessary. If you need to, make sure to hide it on your person or “camouflage” it (label a data CD as a pop music CD). See Sneakernet.
- Internet Cafes
- Assume you are being watched.
- Assume computers at cyber cafes are tracking key strokes and capturing screenshots.
- Avoid cyber cafes without an easy exit and have a contingency plan if you need to leave rapidly.
Digital Security Technologies
When combine with the tactics described above, the following technologies can help you stay safe and keep your data relatively more secure.
- Mobile phones
- Use CryptoSMS, SMS 007 or Kryptext to text securely (this requires java-based phones).
- Use Android Guardian as soon as it becomes available.
- Access mobile versions of websites as they are usually not blocked. In addition, connecting to mobile websites provides for faster connections.
- Digital cameras
- Use scrubbing software such as: JPEG stripper to remove the metadata (Exif data) from your pictures before you upload/email.
- Have a safe Secure Digital Card (SD) that you can swap in. Preferably, use a mini SD card with a mini SD-SD converter. Then place the mini SD into a compatible phone for safekeeping.
- Computers/Laptops
- Use an effective anti-virus program and ensure it updates itself online at least once a day: TMIS, McAfee, Symantec/Norton, AVG, Avira, NOD32, Kaspersky.
- Do not use illegal, cracked, hacked, pwned, warez software.
- Keep your software programs (operating systems, productivity suites, browsers) up-to-date with the latest software updates.
- Use software to encrypt your hard drive: Bitlocker, TrueCrypt, PGP Whole Disk Encryption, Check Point, Dekart Private Disk.
- Use a different file type to hide your sensitive files. For example, the .mov file extension will make a large file look like a movie.
- Mac users can use Little Snitch to track all the data that goes into and out of your computer.
- From a technical perspective, there’s no such thing as the delete function. Your deleted data is eventually written over with new data. There are two common ways to wipe sensitive data from your hard drive or storage device. You can wipe a single file or you can wipe all of the ‘unallocated’ space on the drive. Eraser is a free and open-source secure deletion tool that is extremely easy to use.
- Flash disks
- StealthySurfer USB Flash Drive
- The secure browsing Tor software can be installed on flash disk.
- Using a USB watch calls less attention as do the USB ear rings and this credit card USB flash disk.
- Email communication
- Browsers and websites
- Use Firefox and get certain plugins to follow website tracking such as ghostery and adblock, adart to remove ads/trackers.
- User Tor software or Psiphon to browse privately and securely.
- I shan’t list access points for secure browsers, Proxy servers and VPNs here. Please email me for a list.
- Always use https in “Settings/General/Browser Connection.”
- VoIP
- Use Skype but not TOM Skype (Chinese version). Note that Skype is not necessarily 100% secure since no one has access to the source code to verify.
- Off The Record (OTR) is a good encryption plugin. For example, use Pidgin with OTR (you need to add the plug-in yourself).
- Gizmo offer encryption for voice conversations, and then only if you are calling another VoIP user, as opposed to a mobile or landline telephone. However, because neither application is open-source, independent experts have been unable to test them fully and ensure that they are secure.
- Adium is a free IM application for Macs with built-in OTR encryption that integrates most other IM applications.
- Blogs and social networking platforms
- There are no safe social networks. The best way to be safe on a social network is fake account and a proxy server.
- The anonymous blogging platform Invisiblog no longer exists, so the best bet now is WordPress + Proxy (preferably Tor) + anonymity of content.
- Log out of facebook.com when not using the site.
- File sharing
- Use Drop.io to create a private, secure media sharing site.
- Use BasecampHQ with secure/SSL option to create more specific usernames and passwords for each user or remote site.
- Internet Cafe
- Other potential tech
Conclusion
The above material was collected in part from these sources:
- Tactical Tech’s Mobiles-in-a-Box and Security-in-a-Box;
- MobileActive’s Mobile Security
- FreeBeagles;
- FLOSS Manuals;
- Feedback from DigiActive and Digital Democracy;
- Personal experience and that of other colleagues in the field.
As mentioned above, please send suggestions and/or corrections as well as updates. And again, please do check the comments below. Thanks!
#iranelection: the revolution will b twtrd.
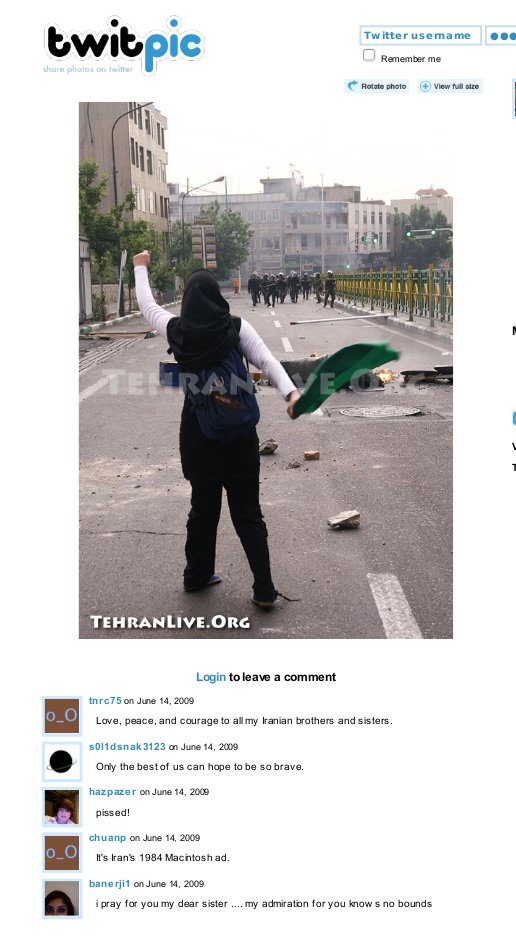 99% of the time twitter is TWOTer (Total Waste of Time). Then comes #cairospeech or #iranelection.
99% of the time twitter is TWOTer (Total Waste of Time). Then comes #cairospeech or #iranelection.
The Daily Dish reports that the Iraninan regime has locked down all other communications, but Twitter is live.
Follow the events on #iranelection
And on http://iran.twazzup.com/
renjie has a list of Twitterers posting from inside Iran (via Reddit)
follow them. show them that they are not alone.
Listen to Eric Lee
Finally. Someone says it out loud. Its not about the platform, the flash, the wiz, the bang. Its about getting unions – or any action group for that matter – to own their site. Owning it just like they own their placards and paint.
SO if they want a blog, give them a blog. If they want a FB page (yuck) let them have it, as long as they make it themselves.
Free Meryem Özsögüt!
An urgent call for action from LabourStart:
Ms. Meryem Özsögüt, trade union leader and management board member of PSI‘s affiliate SES in Turkey (the trade union of public employees in health and social services) was arrested on the morning of 8 January following her participation in a press conference on 14 December 2007 to denounce the killing by the police of activist Kevser Mizrak.
You can help! Sign the petition. Join the campaign.
I’m on da map
Search web2.0 in London on google maps. What do you get?

I kid you not.
But you can hack your own.
(digg)



















